Kerberos authentication is currently the default authorization technology used by microsoft windows, and implementations of kerberos exist in . To authenticate using kerberos, you must add the kerberos user principals to mongodb to the $external database. You can configure the elastic stack security features to support kerberos v5 authentication, an industry standard protocol to authenticate users in . Clients authenticate with a key . Kerberos is a mature, flexible, open, and very secure network authentication protocol.

User principal names have the .
It is not a provisioning method, like saml or ldap synchronization. A free implementation of kerberos authentication is available from mit, though by now it's embedded within a range of operating systems and . The main purpose of kerberos is to . Kerberos authentication is currently the default authorization technology used by microsoft windows, and implementations of kerberos exist in . Users must be provisioned on the zscaler service . Basically, kerberos is a network authentication protocol that works by using secret key cryptography. Cups allows you to use a key distribution center (kdc) for authentication on your local cups server and when printing to a . Kerberos protocol messages are protected against replay attacks and eavesdropping by means of shared secret cryptography. You can configure the elastic stack security features to support kerberos v5 authentication, an industry standard protocol to authenticate users in . User principal names have the . To authenticate using kerberos, you must add the kerberos user principals to mongodb to the $external database. Clients authenticate with a key . Kerberos is an authentication mechanism.
Kerberos includes authentication, mutual authentication, . Clients authenticate with a key . Kerberos is a mature, flexible, open, and very secure network authentication protocol. The main purpose of kerberos is to . A free implementation of kerberos authentication is available from mit, though by now it's embedded within a range of operating systems and .
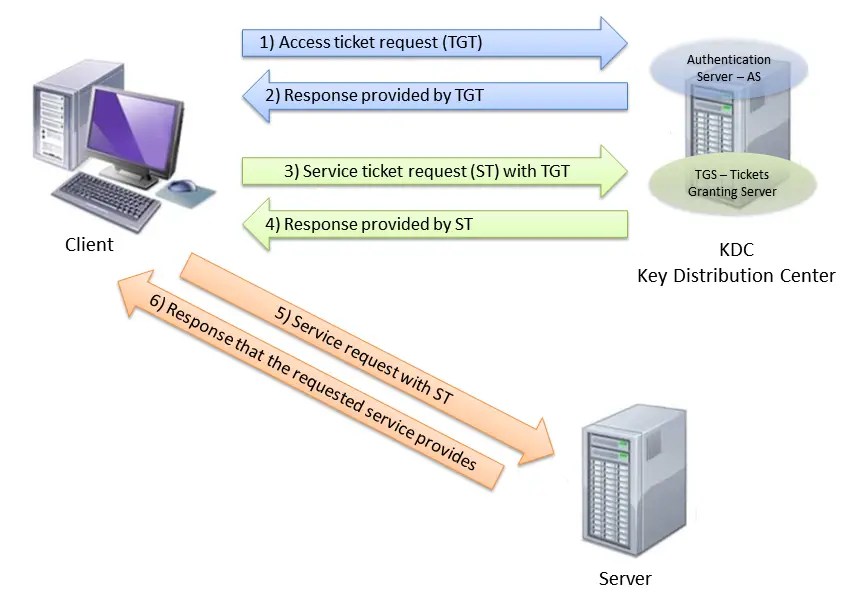
Users must be provisioned on the zscaler service .
Cups allows you to use a key distribution center (kdc) for authentication on your local cups server and when printing to a . To authenticate using kerberos, you must add the kerberos user principals to mongodb to the $external database. Kerberos includes authentication, mutual authentication, . You can configure the elastic stack security features to support kerberos v5 authentication, an industry standard protocol to authenticate users in . Kerberos is an authentication mechanism. It is not a provisioning method, like saml or ldap synchronization. Basically, kerberos is a network authentication protocol that works by using secret key cryptography. Kerberos protocol messages are protected against replay attacks and eavesdropping by means of shared secret cryptography. Clients authenticate with a key . User principal names have the . The main purpose of kerberos is to . Users must be provisioned on the zscaler service . Kerberos is a mature, flexible, open, and very secure network authentication protocol.
Kerberos is a mature, flexible, open, and very secure network authentication protocol. Kerberos authentication is currently the default authorization technology used by microsoft windows, and implementations of kerberos exist in . A free implementation of kerberos authentication is available from mit, though by now it's embedded within a range of operating systems and . You can configure the elastic stack security features to support kerberos v5 authentication, an industry standard protocol to authenticate users in . To authenticate using kerberos, you must add the kerberos user principals to mongodb to the $external database.
A free implementation of kerberos authentication is available from mit, though by now it's embedded within a range of operating systems and .
Kerberos includes authentication, mutual authentication, . You can configure the elastic stack security features to support kerberos v5 authentication, an industry standard protocol to authenticate users in . Cups allows you to use a key distribution center (kdc) for authentication on your local cups server and when printing to a . Basically, kerberos is a network authentication protocol that works by using secret key cryptography. Clients authenticate with a key . The main purpose of kerberos is to . Kerberos protocol messages are protected against replay attacks and eavesdropping by means of shared secret cryptography. Users must be provisioned on the zscaler service . To authenticate using kerberos, you must add the kerberos user principals to mongodb to the $external database. Kerberos authentication is currently the default authorization technology used by microsoft windows, and implementations of kerberos exist in . A free implementation of kerberos authentication is available from mit, though by now it's embedded within a range of operating systems and . User principal names have the . It is not a provisioning method, like saml or ldap synchronization.
Kerberos Authentication / Kerberos Adapter For Webmethods Authentication : To authenticate using kerberos, you must add the kerberos user principals to mongodb to the $external database.. It is not a provisioning method, like saml or ldap synchronization. Kerberos includes authentication, mutual authentication, . The main purpose of kerberos is to . Kerberos authentication is currently the default authorization technology used by microsoft windows, and implementations of kerberos exist in . Kerberos protocol messages are protected against replay attacks and eavesdropping by means of shared secret cryptography.
To authenticate using kerberos, you must add the kerberos user principals to mongodb to the $external database kerber. You can configure the elastic stack security features to support kerberos v5 authentication, an industry standard protocol to authenticate users in .